What are Security Audits in Blockchain?
In the evolving field of cryptocurrencies, security holds importance for trust and sustainability. Security audits function as vigilant guardians patrolling the landscape. Emphasising their importance cannot be overstated. They serve as safety nets safeguarding investors, developers, and users against the risks that exist within the world.
Operating on a decentralised ledger system, blockchain is the disruptive technology that powers things like Bitcoin and Ethereum. It offers trust, immutability, and unparalleled transparency. However, this decentralised style doesn’t save it from security risks. Even with all that’s at stake in the form of digital assets, vulnerabilities and weaknesses can be found throughout components like consensus mechanisms, smart contracts, etc. This can lead to losses so monumental it erode the trust within the crypto community.
Cryptocurrencies have revolutionised the system. This liberation is not without its challenges. Security audits act as the line of defense in protecting user funds security. They establish trust by assuring members of the ecosystem that their investments are secure and legitimate. These audits navigate projects through a web of compliance to ensure adherence to applicable laws.
These audits proactively identify flaws in contracts, blockchain networks, and decentralised apps (DApps) before actors can exploit them. Security audits contribute to a more resilient and secure crypto environment by detecting these vulnerabilities.
Being at the forefront of blockchain security is Codiste. They bring industry-leading tools alongside an unwavering commitment to protecting the crypto world. In this guide, we will understand blockchain security audits in-depth and Codiste’s approach to fortifying blockchain systems against any threat that comes its way.
Through this blog, you will understand how security audits play a role, in the cryptocurrency world. Equipped with this knowledge you will be empowered to make decisions and protect your assets within this dynamic and ever-changing landscape.
Join us on this journey as we collaborate to safeguard the future of cryptocurrency.
What is a Smart Contract Audit?
Smart contracts are technically coded in programming languages that are specific to the blockchain. They also execute on a decentralised virtual machine. The significance of smart contracts is their ability to enhance transparency, security, and trust within the ecosystem. This causes a lasting impact that can revolutionise whole industries like finance and healthcare. Anyone who wants to get into blockchain needs to recognize these intricacies as smart contracts represent what makes the technology so groundbreaking.
Smart contracts are automated agreements where contract terms are directly embedded into code. They play a role in the cryptocurrency industry by streamlining transactions, reducing reliance on intermediaries, and boosting trust. It is vital to ensure their security which can be done by conducting a smart contract audit.
And, How Smart contract audit can be done?
- Code Examination and Analysis
The audit process commences with a review of the contract code to uncover any potential flaws or vulnerabilities. The quality of the code and adherence to established practices are assessed. - Identification of Vulnerabilities
Security experts identify vulnerabilities like reentrancy attacks and integers. Unauthorised access could compromise the contract’s integrity. - Risk Assessment
Auditors assess both the severity of identified vulnerabilities and their potential impact, on the contract and its users. A risk rating is assigned to prioritise fixes.
Here are a few real-world instances of smart contract vulnerabilities –
As per one of the MDPI researches, in 2016 there was an attack on DAO that exploited a weakness resulting in the theft of millions of dollars. In 2017 there was a problem with the Parity wallet where money got locked due to a software issue. Moreover, various DeFi attacks have taken place where smart contract vulnerabilities were exploited for gains.
What are Best Practices for Developing Secure Smart Contracts?
To keep smart contracts safe, developers need to follow a set of best practices. These practices were built using two foundations, sound software engineering principles and blockchain technology. These practices have three main parts, testing, code audits, and vulnerability assessments. Each part was made to avoid one thing: common pitfalls like attacks and overflow.
To further add security, formal verification techniques and leveraging security tools should also be used early in the development process to identify issues that could happen later on. In a nutshell, these practices will not only make the smart contract reliable but also secure enough to protect the entire blockchain ecosystem from harm.
Below are the best practices for developing secure smart contracts for your business –
- Stick to established code standards like Solidity practices.
- Utilise automated tools for code analysis and testing.
- Implement appropriate access control methods.
- Incorporate security libraries. Tested code into your development process. Whenever possible, consider verification.
- Conduct audits. Make necessary modifications as the contract evolves.
How can Competitive Audits help companies in adapting to changes in the competitive market?
A competitive audit involves analysing the strengths and weaknesses of competitors in the crypto industry. They hold importance as they provide insights into market positioning, help identify opportunities, and allow organisations to adapt and refine their plans to gain a competitive edge.
Here’s how you can conduct an audit in the crypto industry:
- Identify Competitors
Start by identifying competitors in the cryptocurrency market such as exchanges, projects, or platforms operating in the same domain. - Gather Information
Collect information about your competitor’s products, services, user base, market share, marketing strategies, and financial performance. - Analyze Marketing and Branding
Study your competitor’s branding efforts, messaging, and online presence including social media platforms to gain an understanding of their market positioning. - Evaluate Technical Aspects
Examine the aspects of your competitor’s solutions like technology implementation security measures employed and unique features offered. - Utilising Competitive Audit Findings for Strategic Advantage
Analysing a competitor’s strengths and weaknesses is imperative to achieve an edge over them.
Here’s what you must know about your competitors –
- Competitors Strengths
Determine areas where your competitors excel such as user experience, design, security measures implemented, successful collaborations, or breakthrough technologies adopted. - Weaknesses
Identify areas where your rivals might have weaknesses such as scalability concerns faced by them regulatory compliance issues encountered or any shortcomings in customer service provision.
So, how can you leverage competitive audit findings as your strategic advantage –
Utilise the insights from the audit to enhance your business plan. Take advantage of your competitor’s weaknesses by offering solutions or addressing areas of pain.
Copy strategies. Adapt them to fit your unique value proposition.
Stay aware of the landscape. Adjust your strategy accordingly to maintain a competitive edge.
Security Audit for Tokenization
Tokenisation is the process of exchanging sensitive data with unique identification symbols, which is known as a “token.” It is also the process of converting world or digital assets into tokens on a blockchain. These tokens serve as representations of ownership or value and can be easily traded or transferred. Tokenization technology can be used to keep sensitive data secure in databases or systems without compromising its security.
It is an aspect of cryptocurrencies that enables ownership and enhances liquidity for various types of assets. While, if we talk the ‘security audit for tokenization’, it includes an investigation of the processes and systems whether secure implementation of tokenization is done properly or not. Security audit for tokenization also ensures to identify and rectify vulnerabilities that occurred during the tokenization process to minimise the risk of data exposure or unauthorised access.
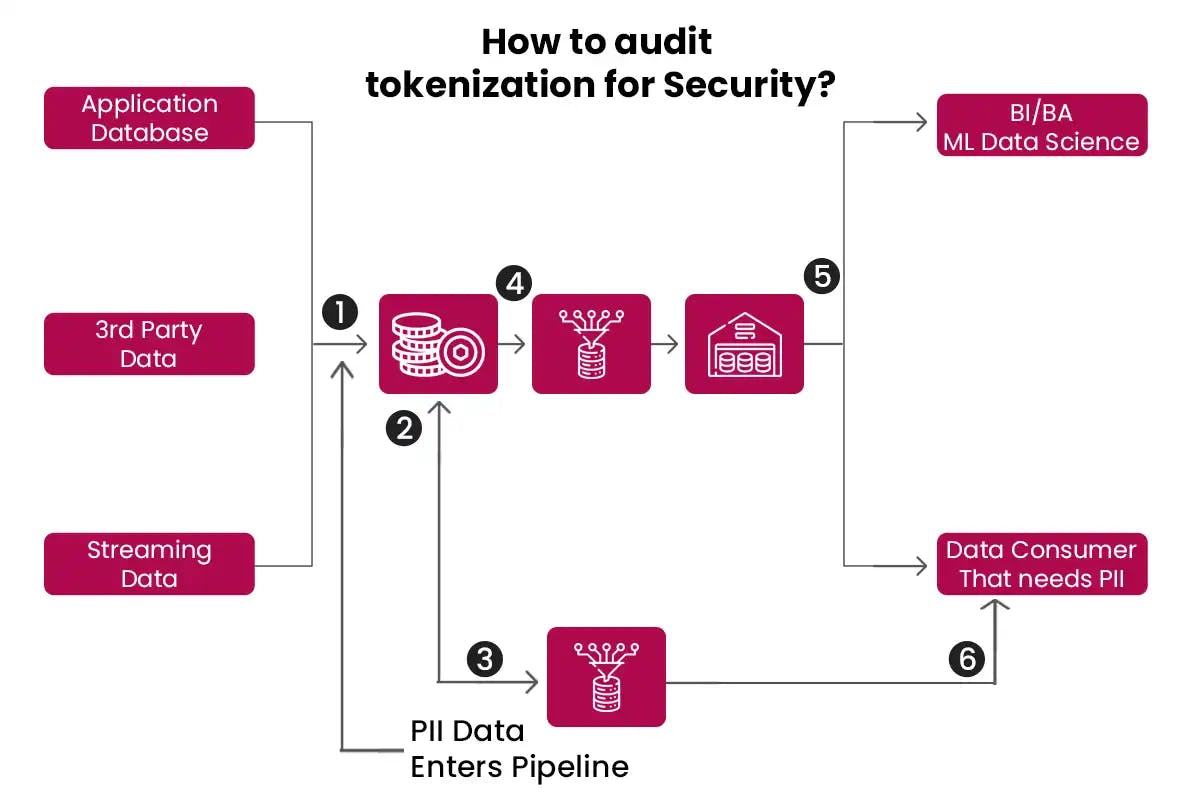
The below image shows that Plaintext-to-token Mapping is Stored in a Secure Data Store:
Steps to Conduct a Security Audit for Tokenization
- Define Objectives
Clearly outline the scope and objectives of the audit specifying which tokens smart contracts and systems will be assessed. - Code Review
Thoroughly examine the contracts that govern tokens to identify any vulnerabilities such as reentrancy, overflow, or access control issues. - Custody Assessment
Evaluate how tokenized assets are stored and secured ensuring robust custody solutions are in place.
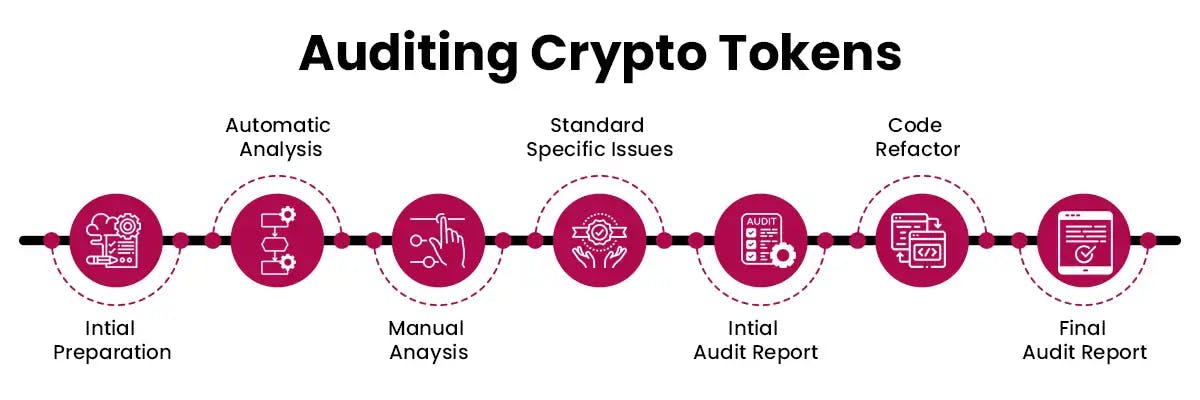
Security Challenges Associated with Tokenization
Tokenization presents security challenges, which include –
1. Vulnerabilities that may exist in the contracts governing tokens.
2. Ensuring custody and secure storage of assets.
3. Meeting regulatory compliance requirements for issuing tokens.
4.Mitigating the risks associated with fraud and hacking within tokenized ecosystems.
Case Study of Security Audits in Blockchain
Tokenization Security Audit Success Stories
In the world of crypto, tokenization has completely changed the ways assets are managed and transferred. Before this, success stories were limited to how much you can buy or sell a coin for. Real estate and artwork have kind of sat in the background until now. Now though, tokenization offers new possibilities for ownership and liquidity.
There are new opportunities that come with these things. But they also have huge security concerns. To make sure everything is safe and trustworthy, tokenization security audits became a necessity.
One of the most popular uses for tokenization came in real estate. One development company thought about making it easier for people to afford condominiums by using fractional ownership and smart contracts. They didn’t forget about security though. Before launching the project, they understood that they had to do a thorough audit on their approach.
Mitigating Vulnerabilities in Network Protocols
- Implement encryption techniques and strong authentication mechanisms to safeguard data during transmission.
- Regularly. Patch network protocols to address known vulnerabilities.
- Conduct penetration. Vulnerability assessments to identify and rectify points in network security.
- Educate participants about communication practices within the network.
- Implement monitoring systems at a network level along with intrusion detection systems for identification and response to threats.
Conclusion
The world of blockchain technology is filled with twists and turns. Just when you think you mastered it, another curve ball is thrown. These changes are the reason security audits are important. They’re the backbone of trust in cryptocurrencies, ensuring blockchain systems stay resilient to threats. In this guide, we’ll turn our attention to Codiste’s dedication to auditing for technical intricacies that strengthen this transformative technology.
Most auditors stop at the conventional boundaries. However, Codiste, being a Top blockchain development company, takes a step further by bringing advanced technical expertise into every part of their work. It doesn’t matter if it’s the underlying infrastructure or individual components that come together as one.
Smart contract audits are where their skills shine the brightest. These contracts act as the foundation of decentralised apps and are examined inch by inch by Codiste’s experts. They have a deep understanding of blockchain-specific programming languages and couple that with comprehensive code reviews and formal verification methods to make sure no vulnerability falls through the cracks while you are approaching them for custom blockchain development service.
With smart contracts, the only thing more important than making sure they work is how secure they are. Codiste ensures their audits leave no stone unturned in that regard.
But Codiste isn’t just a one-trick pony, they also make sure the network running the blockchain, along with all of its components, can withstand an attack. It’s not enough to stop after ensuring smart contracts are safe since a system for a decentralised network needs to be safe throughout. Codiste is always prepared for new threats too. Their blockchain development team constantly adjusts and creates new methods of security so that blockchain projects of all sizes can trust them.
And as big as it is now, the blockchain space will only grow and develop further. Going forward Codiste by hiring blockchain developers plans to stay at the forefront of innovation and improvement. Ultimately security audits serve as the basis for establishing a reliable crypto environment. They go beyond being protocols; instead, they embody a dedication to safeguarding the future of finance. By implementing practices and maintaining surveillance through security audits we can navigate towards a more secure and prosperous future, in the evolving crypto ecosystem.